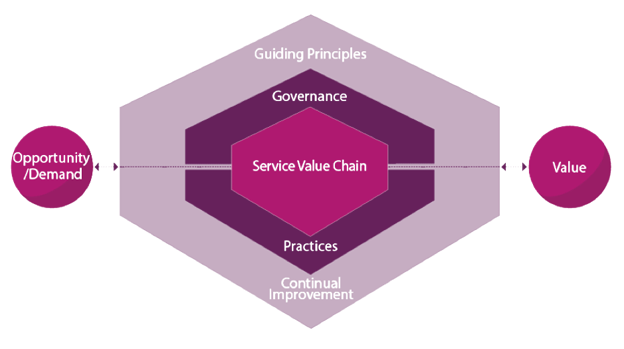
Implementing Cybersecurity, Part 4: What do you get when you tie all three together?
Over the last few articles we talked about how ITSM systems help Tirihanna with password changes and maintaining her work station. We talked about how her lack of training caused major issues. And we talked about the various security processes READ MORE