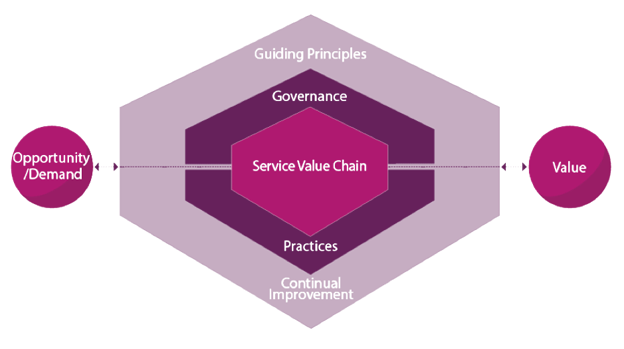
The Implementation of ITSM: Seemingly Simple, Deceptively Difficult
In our last two blog posts, we discussed ITSM and NIST and how they apply to your organization’s cybersecurity. Now we are going to show you how the implementation of an ITSM strategy forms the base to layer NIST policy READ MORE